Gabriel Aguiar Noury
on 13 August 2021
Open Source Robotics Challenges – Planning for Security
Open Source Robotics Challenges is a series of blogs that will share guidelines and advice for open source companies to overcome market barriers.
We will touch on topics regularly raised by companies in our open source community such as security awareness, prototyping strategies, safety architecture, adoption and more. Our aim is to help organisations overcome the barriers associated with open source adoption in robotics so they can experience the inherent benefits that come with open source technologies. Agility, modularity and adaptability are some of the biggest benefits that open source robotics has been bringing to the field. This first blog will talk about security and security compliance.
Security in open source robotics
Scans of the entire IPv4 address space of the Internet for instances of the Robot Operating System (ROS) have identified several hosts supporting ROS that are exposed to the public Internet [1]. Thereby allowing anyone to access robotic sensors and actuators. Researchers have exploited this access with the consent of participants to demonstrate the lack of security in open source robotics. These researchers successfully broke in and read image sensor information and actuated the physical robots.
More alarming are the results from a survey to domain experts around industrial robot controller implementation [2] [3]. The studies show that from both academia and industry, 30% of participants had robots accessible from the Internet, while 76% had never performed a professional cybersecurity assessment. It just seems like we don’t care.
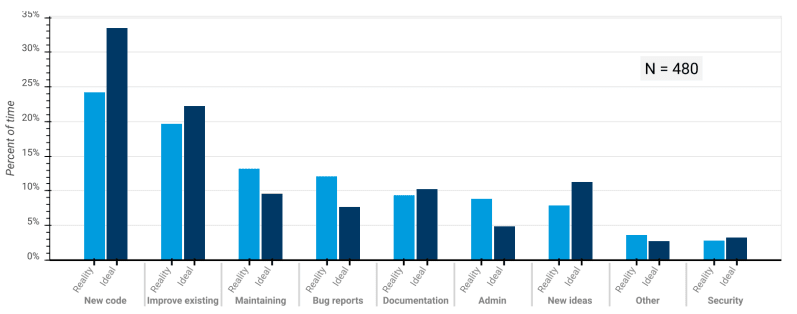
Open source Software Contributor Survey
Take for instance the Report on the 2020 Free Open Source Software (FOSS) Contributor Survey [4]. With a total of 1,196 respondents from the most widely used open source projects, it found that respondents spend very little time on responding to security issues; an average of 2.27% of their total time spent working on their project. Moreover, the respondents do not report a desire to increase this significantly; in fact, the average time they would like to spend on security was only 0.06% higher. Some respondent comments, such as “I find security an insufferably boring procedural hindrance”, clearly illustrate this concerning situation.
Security in robotics should be a priority.
We know that attackers try to enter through any connection to a network – even robots. Robots, just like any other device connected to an organisation network could be breached opening risks to other devices in the network. The reality is that it’s widely known that ROS1 doesn’t support encryption allowing attackers to enter your system. We should place the same importance on preventing these attacks as we do in building our solutions.
Security issues: use cases & example
Disconnecting devices from the internet is no longer protection from remote attackers. It is irresponsible for us to place vulnerable robots behind firewalls and claim they are safe. We have already seen malware that breaches isolated networks. For instance, Stuxnet [5]. But that was almost ten years ago. Today’s malware is far more effective. If the malware has a hold on a network and your robot is the unpatched link, your robot will open the door to attackers.
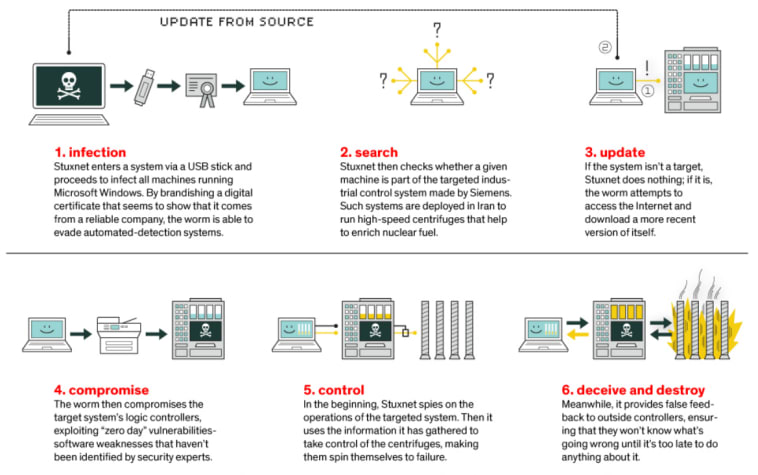
No internet, no problem. History has shown us that vulnerabilities can always be exploited. Image taken from The Real Story of Stuxnet.
Do you think that connecting a corrupted USB to a computer is unlikely? Well, let’s check another example. What about clicking a malicious web link with a phone? A new version of a known network-address translation (NAT) slipstreaming attack has been uncovered, which would allow remote attackers to reach multiple internal network devices, even if those devices don’t have access to the internet.
Here you can see a video of how it works. See how easily the system is breached. In a matter of minutes, the attacker can change the logical program running PLC and alter the digital outputs.
The ability to reach devices without human interaction means that attackers can reach not only desktops but also other devices that don’t typically have human operators — unmanaged devices like printers, industrial controllers, Bluetooth accessories, IP cameras, sensors, smart lighting and more. The impact of an attack on these can be severe, ranging from denial-of-service (DoS) to a full-blown ransomware attack.
What can open source robotics companies do?
The risks are real, but they can be minimised.
A synopsis report found that 84% of these codebases had at least one vulnerability, with the average having 158 per codebase. Most OSS vulnerabilities are discovered in indirect dependencies (Snyk). A typical vulnerability can go undetected for 218 weeks, and on average takes 4 weeks to get resolved once the project is alerted to it.
As explained by Jennifer Fernick, SVP and head of global research at NCC Group, at a time when the time between vulnerability disclosure and exploit creation has gone from 45 days to 3, “the number of vulnerabilities in the wild outpaces the speed at which the security community can patch or even identify them,” and automated attacks are quickly weaponizing even little-publicised flaws.
Organisations must secure every link or device in a network or system to secure the most important parts of their organisation. By using the basic tools to ensure that each access point is secure, they severely mitigate the risks and costs of an attack. It’s important to spend some time making sure all access points are well-secured. For this defence, security for robots is crucial. https://ubuntu.com/engage/securing-ros-on-robotics-platforms-whitepaper

To make sure your robot security is compliant and secure, there are processes you can follow. These protocols help mitigate risks and provide a structured approach that makes security even easier. Several ROS companies are succeeding due to these fundamental considerations.
To prevent exploits – loss of information, value or time – a security framework must be implemented. These frameworks provide a set standard for security controls. They are used to maintain security across a company so attackers can’t gain a foothold in a seemingly unimportant part of the system.
What are CIS and NIST?
CIS stands for the Center for Internet Security. CIS sets up security benchmarks from a community consensus. It’s created by the same people who use it every day so you know it works. The CIS 20 provides the top 20 controls used in the framework. It won’t lock down your system and it’s constantly being updated over time. All of these resources are free and open to the public. You can find them here.
For ROS within CIS, we have a benchmark for ROS melodic that runs on Ubuntu 18.04. It contains over 200 recommended settings for securely operating ROS. You can even pull out everything in the guide as a separate spreadsheet. That can be found here.
In comparison, NIST is used for more enterprise-wide systems. It gives recommendations on how to handle cybersecurity in an enterprise-focused setting. This is also used around the globe. It is organised into three primary components, the core, the tiers, and the profiles. The core can be described as a collection of security controls. The tiers indicate the extent to which cybersecurity management is tied and integrated into business needs and practices. The profiles are a customisation tool; they organise the security controls in a way to allow organisations to differentiate between current and target states, or deploy different profiles to different parts of the organisation. For security controls, the framework points to other standards, such as CIS, NIST SP 800-53, and others.
The implications for your business
Does a small to medium-size open source robotic company need to consider a security paradigm and compliance with a cybersecurity framework? Think about the legal implications and the risk involved. Sometimes, depending on the field, you simply need to comply because of regulations. Take for instance the finance sector, companies need to comply with PCI standards. Or the health sector in the US, and its compliance with HIPAA. Everyone in Europe needs to follow the GDPR. In practice the answer is complicated as organisations often provide services or act as a supply chain to other organisations, passing the requirements to all involved parties.
The risk approach requires that key people in the company understand the business need for reducing cybersecurity-related risks. Small and medium-sized enterprises (SMEs) are more likely to say that upgrading IT and data security to boost corporate resiliency is a top priority according to the 2020 Security Priorities Study, which demonstrates the inherent agility advantage of small and medium-sized businesses (SMBs).
Ultimately, you can not simply avoid the conversation. Lack of security could cost you sales, users’ confidence and new market opportunities. Ultimately stopping you from scaling. Overlooking security at the initial stages of production is reckless. Security by design should be the mentality of any open source engineer.

Learn more about open source robotics security for enterprise
If you want to learn more about the value of cybersecurity frameworks and list the available options, please read our small to medium-size business guide to cybersecurity.
If you want to learn more about security maintenance for ROS, please read our security maintenance and enterprise support for your ROS environment.



