Nikos Mavrogiannopoulos
on 18 January 2022
The CIS benchmark has hundreds of configuration recommendations, so hardening and auditing a Linux system manually can be very tedious. Every administrator of systems that need to comply with that benchmark would wish that this process is easily usable and automatable. Why is that? Manual configuration of such a large number of rules leads to mistakes – mistakes that cause not only functional problems, but may also cause security breaches. In fact, one of the top reasons for security breaches the last few years is due to misconfigurations, according to Verizon data breach investigations.
Let us introduce the Ubuntu Security Guide (USG). The Ubuntu Security Guide is a new tool available on Ubuntu 20.04 LTS that makes automation easy and greatly improves the usability of hardening and auditing with CIS, while allowing for environment-specific customizations. In the rest of this blog, we go through the major use cases such as CIS compliance, audit, and customization.
Key benefits or, why should I care?
While observing how our existing CIS compliance tools were being used by auditors and administrators of Ubuntu systems, we identified several points that would improve their workflow. The following list summarizes the main pain points for audit and compliance workflows that are addressed by Ubuntu Security Guide.
With Ubuntu Security Guide
- you can customize (tailor) the CIS profile; select the CIS rules to comply with.
- you can select a specific version of the CIS benchmark, i.e., a tooling upgrade doesn’t need to break scheduled scans that target a specific benchmark version.
- teams can standardize on a profile by storing it in a hard-wired location, preventing the case of different people accidentally scanning or complying with different profiles or versions.
- the same experience applies whether scanning for the CIS benchmark, DISA-STIG and any other profiles made available in the future.
- last but not least, you use a consistent interface across Ubuntu releases.
Let us now take a deep dive into using the Ubuntu Security Guide.
How to install the Ubuntu Security Guide
The Ubuntu Security Guide is available with a subscription. Once the subscription is attached on your Ubuntu system, install USG with the following commands:
$ sudo apt update
$ sudo apt install ubuntu-advantage-tools
$ sudo ua enable usg
$ sudo apt install usgHow to audit the system
At the time of this writing, the corresponding CIS benchmark for Ubuntu 20.04 LTS is the “CIS Ubuntu Linux 20.04 LTS Benchmark v1.0.0”. We will audit our system using USG and that benchmark with the following command.
$ sudo usg audit cis_level1_serverThis will generate a report placed in /var/lib/usg with the results of the audit. The HTML report contains the list of rules that succeeded and failed, and looks like the following screenshot.
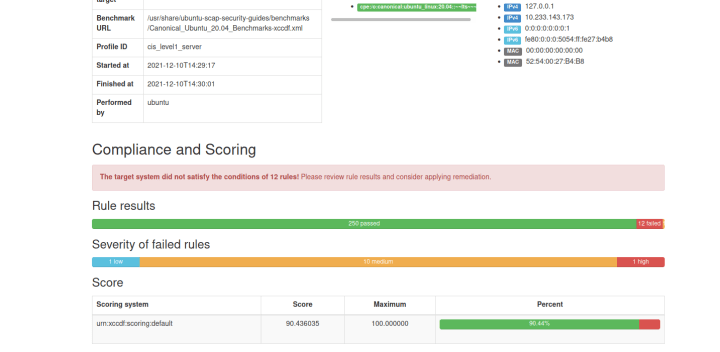
What was the “cis_level1_server” command line option that we used? It indicates the USG profile name to use for audit. These profiles correspond to the CIS profiles with hardening tailored towards workstations vs. server systems, and a higher level indicates more rules that further reduce the attack surface of a system, but at the cost of reducing usability.
| USG profile name | Corresponding CIS profile |
|---|---|
| cis_level1_workstation | Level 1 Workstation profile |
| cis_level1_server | Level 1 Server profile |
| cis_level2_workstation | Level 2 Workstation profile |
| cis_level2_server | Level 2 Server profile |
How to modify the system for compliance
Modifying a system to comply with the CIS benchmark with USG is as simple as the following command.
$ sudo usg fix cis_level1_serverAnd that’s all. Performing an audit after a reboot will reveal that the compliance level has increased significantly!
How to create a custom profile based on CIS
Compliance with a benchmark is not an all-or-nothing task. Each environment is different, and options that are considered as niche in one place can be essential in another. As such, USG allows tailoring the profile and removing unnecessary rules, as well as customising the rules that have multiple options available.
You can customise a profile using a tailoring file, as demonstrated below.
1. Generate a tailoring file:
$ sudo usg generate-tailoring cis_level1_server ./tailor.xml
2. Edit the tailoring file and go through the rules shown as comments. For example, to set the remote auditd server (rule UBTU-20-010216), find the text:
<!-- UBTU-20-010216
<xccdf:set-value idref="var_audispd_remote_server">logcollector</xccdf:set-value>
And replace the logcollector with the name of the server. To disable the rule, replace “selected=true” with “selected=false”.
3. Audit using the new tailoring file:
usg audit --tailoring-file tailor.xml
4. Fix using the new tailoring file:
$ sudo usg fix --tailoring-file tailor.xml
In the example above we set the name of the server that acts as a log aggregator. Let us now examine how we can disable certain rules from applying by using the default tailoring file.
The default tailoring file
Let’s say that we are in an environment where we require the jffs2 filesystem, but we also need to comply with the CIS level 1 for server that prohibits it. At this time we will create and use the “default” tailoring file in /etc/usg/default-tailoring.xml. If that file is present, it acts as the default profile for the system and will be used by the `usg` fix and audit commands without a need to specify a profile.
1. Generate a tailoring file:
$ sudo mkdir -p /etc/usg
$ sudo usg generate-tailoring cis_level1_server /etc/usg/default-tailoring.xml
2. Edit the tailoring file and go through the rules shown as comments. Let’s try to find jffs2 in that file:
<!-- 1.1.1.3 Ensure mounting of jffs2 filesystems is disabled (Automated) -->
<xccdf:select idref="kernel_module_jffs2_disabled" selected="true"/>
By replacing the “selected=true” with “selected=false”, we no longer enforce the disablement of the jffs2 filesystem.
3. Audit using the new tailoring file:
$ sudo usg audit
4. Fix the system using the new tailoring file:
$ sudo usg fix
Conclusions
Manually complying with security profiles is a tedious and complex task that is easy to get wrong. The Ubuntu Security Guide (USG) brings simplicity and integrates the experience of several teams working on compliance. It enables the audit, fixing, and customisation of a system with minimal command line options, while enabling a system-wide configuration for compliance for easy management by diverse people in a devops team. The usg tool is available on Ubuntu 20.04 with Ubuntu Advantage or Ubuntu Pro. There are many ways to achieve compliance with the CIS benchmark, some easier than others. The Ubuntu Security Guide is Ubuntu’s way of achieving compliance by providing a familiar, Linux native interface and is based on the OpenSCAP technology. We welcome you to consider giving it a try! More detailed documentation is available at our documentation pages.



